Cybercrime | Network Assessment | Cybersecurity
What to Do After Completing a Cybersecurity Assessment (3 Steps)
Evan has been building, deploying, managing, and protecting enterprise IT solutions for the last 15 years. His "strategy first" approaches to cybersecurity deliver the right amount of protection without breaking the bank and ensure operations stay efficient.
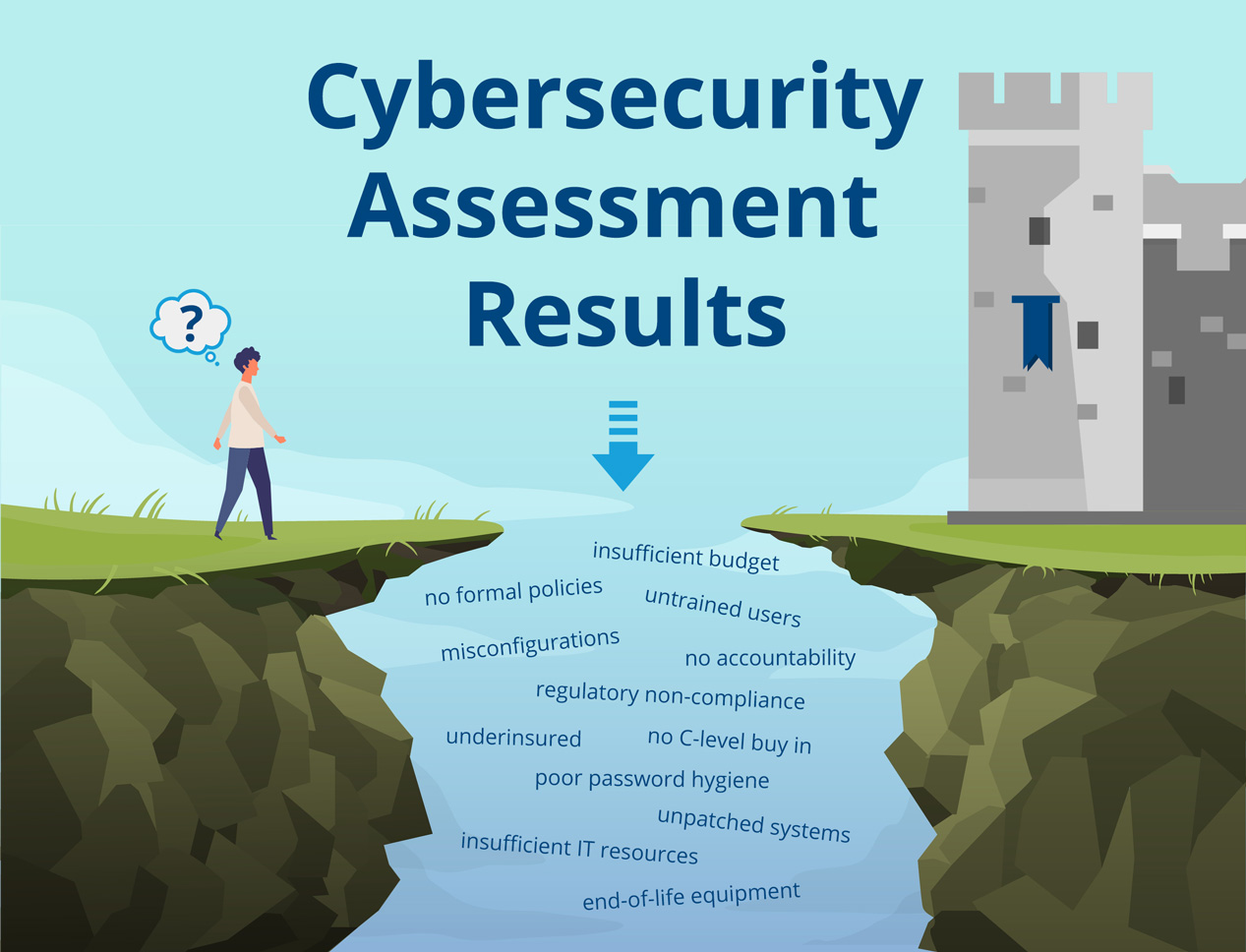
So, your company received a cybersecurity assessment to identify gaps and risks within your network, but now, you’re left wondering how to create an actionable plan with this new knowledge.
Simply identifying the issues isn’t enough to keep the hackers away once they discover vulnerabilities to exploit.
The first thing you need to do is bridge the gap between a cybersecurity assessment and what it is to be a secure business. It’s important to remember, good cybersecurity is never complete and shouldn’t be a one-time response to an assessment.
Every business should have a cybersecurity program that is reviewed and revised semiannually or annually to stay ahead of the game and ahead of bad actors.
CCI Systems is a partner who can help your leadership team while you build your cybersecurity framework. Keeping your company and network safe is a skill our experts have learned over years of experience within the security industry.
Once your company chooses your framework, you will begin to implement your program, and finally, you will develop a strategy to perform program upkeep. By tackling each piece of the cybersecurity framework, your company will be one step closer to a complete plan of action.
Choose Your Security Framework: DIY or Standard
To better hone your cybersecurity framework to your business needs, select one of two paths: Do It Yourself or Adopt a Standard Framework.
The pros and cons of each choice hinge on the stage of growth your company is in, the availability of cash to fund the security initiative, and how much time your technicians have to commit toward executing this framework.
Do It Yourself
| Pros |
| Lower initial investment |
| Works best for very small, simple business models |
| Cons |
| Difficult to communicate externally |
| Risk adherence to outdated practices |
| Risk gaps in policies, procedures, and protections |
Adopt a Standard Framework
| Pros |
| Governing body for the standard framework ensures completeness and relevance of the program |
| Easy to communicate externally |
| May support formal audits and corporate certification |
| Company gains a clear understanding of both technical and legal protections |
| Cons |
| Initial alignment is costly and time-consuming |
| Overly complex for very small businesses |
Choose a Cybersecurity Program
When selecting a cybersecurity program for your business, it’s common to be overwhelmed by the number of implementation options. This can be very difficult for a company that does not fall within a standard framework.
Each business has individual needs to address, so narrowing down the options can become a complex and meticulous process of elimination.
Factors to consider when choosing a cybersecurity program:
- Industry
- Customer base
- Geography
- Cost
- Risks
- Competitor approaches
- Time to deliver
Each factor contributes to the design of your cybersecurity program and helps prioritize the most important pieces.
Implement Your Cybersecurity Program
When implementing your cybersecurity program, there are three main phases: Plan, Implement, and Train.
Laying out each phase will help eliminate any hiccups or bumps in the road you and your team didn’t account for. Anticipating those holes and gaps will speed up the implementation process and save your business time and money.
To reach these goals, use the 3 T’s of Cybersecurity Strategy: Tactics, Talent, and Toolsets. For more information on the 3 T’s, check out CCI’s eBook on the topic.
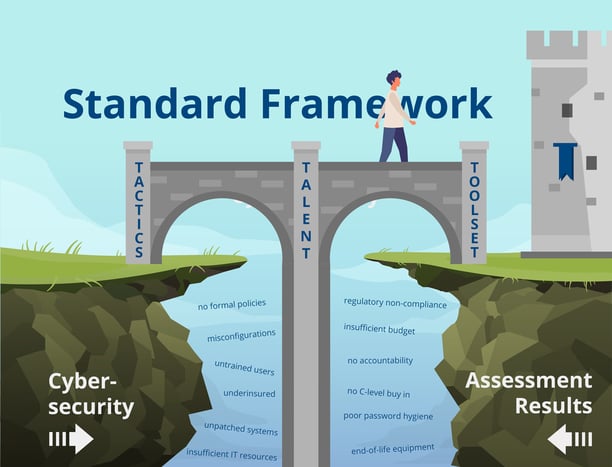
Planning and Communication
Executive-level signoff is crucial for a successful program. Good cybersecurity is cultural, and company culture starts at the top.
Once company executives have signed off, begin creating budgets and timelines with multiple checkpoints. It can be easy to get discouraged, as the implementation process can seem daunting, but checkpoints will help keep you on track.
When making your budgets and timelines, keep the priority list identified during your cybersecurity assessment on hand. This list will help determine what to implement and it will act as a guide throughout each phase.
Creating and Implementing Controls
Based on your timelines, onboard new technologies and manage technical controls. Sticking to each checkpoint will enable a smooth transition without overlooking any specific details.
As controls and technologies are implemented, policies, processes, and procedures must be created that align with your framework. These documents must also align with contractual and regulatory obligations.
Training on Cybersecurity
Ensure that all employees, executives, and key business partners are aware of new policies, processes, and procedures.
Disseminating this information can take the form of email updates, a learning hub where documentation is stored, or assigning material followed by a quiz or test for personnel. More forms of communication are better than less.
Additionally, you must set up a mechanism for communicating future changes to cybersecurity documents, along with any updated training needs.
Perform Program Upkeep
Cybersecurity is a continuous process. As cybercriminals evolve, so too must your business and staff.
A healthy cybersecurity framework should include:
- scheduled framework reviews and updates.
- scheduled policy, process, and procedure reviews and updates.
- creation of annual security budgets.
- internal audit management.
- third-party audit management,
- continuous gap analysis and audit management.
The key to keeping your cybersecurity framework up to date is timelines. Your Red, Blue, and Compliance teams should revisit timelines frequently and stick to them.
By revisiting past timelines, improvements can be made as new technologies become available. Plus, other checkpoints may be altered or eliminated, based on unanticipated changes or events, after the initial timeline was created.
As you’re managing the upkeep of your cybersecurity framework, you may ask, “How will I know if we’re successful?”

Cybersecurity success looks like:
- fewer security incidents.
- higher pass rates on end user security testing.
- 100% audit pass records.
- tracking business obtained because of superior security practices.
- monitoring of business retained due to superior security practices.
- cost tracking.
- lower insurance costs.
Cost of Security Upkeep
At first, maintaining a cybersecurity program can seem very expensive.
There can be especially large upfront costs to implement your framework, and the required overhead can be an immediate non-starter for many companies. Yet, despite the cost of implementation and upkeep, upfront costs are much cheaper than the cost of repairing cybersecurity disasters.
It is estimated that the average cost of a data breach in 2021 will be $4.24 million, according to IBM Security.
How to Act on Your Cybersecurity Assessment
Starting with a cybersecurity assessment is the first leg of your journey into a good and secure cybersecurity strategy.
Taking the knowledge from the assessment and applying each component in a real-world setting can be intimidating and confusing. Other times, implementation can be impossible with limited resources.
The good news is you do not have to do it alone.
CCI has the skills necessary to help you through the cybersecurity process. Our experts can help any company bridge the gap between a cybersecurity assessment and a more secure business.
Whether it’s selecting a cybersecurity framework, implementing the framework, or framework upkeep, CCI can help at any stage.
If your company is looking for a thorough evaluation of your cybersecurity program, or you are seeking a cybersecurity assessment, talk with an expert at CCI

